Attacks on our private information seem to come from everywhere. The worst thing is that perpetrators have thought of a new way to access your data by the time you feel you are on top of the security your devices need.
Where does it stop?
Awareness helps. The type of attack we talk about in this blog is particularly insidious because it can even trick seasoned IT professionals who actively look for malware. If they can be fooled, what hope do the rest of us have?
Malvertisers are particularly crafty with their attacks. Let’s look at their latest strategy to take over your devices.
What is a Malvertiser?
Distributing malware via online advertisements is the purpose of malvertisers. With advertising being a critical source of income for websites, malvertising takes advantage of these growing pathways to reach large online audiences.
Malvertisers use a range of strategies, with the result always being to either direct a user to a malicious server or to get them to download malware onto their device. Online vendors are aware of malvertising strategies and work to prevent their attacks however this is not easy to accomplish.
Let’s go Phishing
Malvertisers use Phishing Kits to lure you in. They are an open-source tool that enables them to create websites specifically for phishing, demonstrating the lengths attackers will go to access your devices and information.
You have seen the types of websites they create, straightforward websites with funny cat pics, trashy stories about celebrities, or blog posts with sensational headlines. These sites are all designed to get you to click on fake adverts that will take you to phishing websites where the aim is to get you to give them your password.
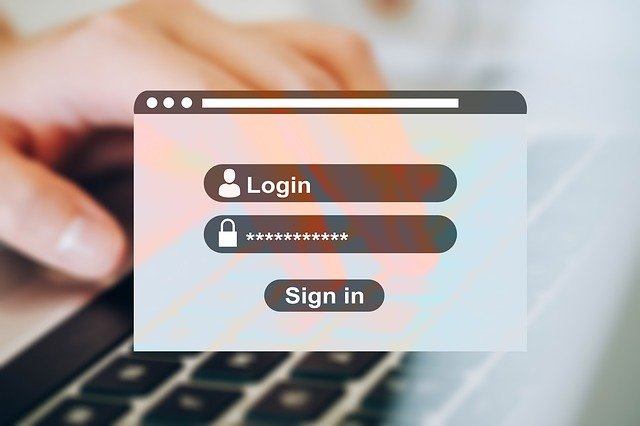
Simulated Login Websites
A new practice, the Browser In The Browser (BITB) Attack, has been uncovered and documented by mr.d0x. See his in-depth explanation about BITB attacks here.
Essentially, the BITB attack involves the malicious player building a website that has a registration and login pop-up that mimics those used for a cloud service like Office365, Facebook, and Google, to name a few. They do this so well that it is likely to fool an IT professional.
It looks so realistic because the pop-up they create has the correct URL, and it looks exactly like the actual window you would use to log in with Facebook and Google. This enables the attacker to collect usernames and passwords to hack accounts.
If you are suspicious about a window you plan to use to log in, try dragging the window. If you can move it to the edge of the browser, it’s real. If not, then you know it is fake.
How to Safeguard Against a BITB Attack
The ONLY way to ensure you are safe against this type of attack is to always use two-factor authentication for all of your online platforms. The reason why 2FA is successful is that if you are a victim of such an attack, the attacker will need the code to access your account, which of course, goes to you and ensures they are locked out.
A Few Last Words
Always think about security with your online presence. The little extra time it takes to implement and use security measures like two-factor authentication is worth spending. Imagine the time, inconvenience, and cost of being successfully hacked. Prevention is undoubtedly worth the effort.
Availability BPA business continuity Business Process Automation Cybersecurity disruption employees Geeks Innovation Internal Security Policies password protection productivity ransomware removal Recovery risk SaaS security Server Uptime SLA Software as a Service Tech Glitches threats Updating Hardware